One of the most simple ways to close a network is to configure your AP to allow connections only from specific wireless network cards.
Each network card has a Mac address just like ethernetcards ,and every Mac address in unique.
Some APs allow you to specify a list of legitimate Mac address. If a machine attempts to join the network with a a trusted Mac address, it can connect; otherwise the request is silently ignored.
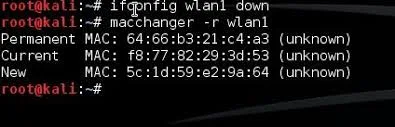
Each card comes with a Mac address hard coded by the vendor. However an attacker can change it trivially by using the ifconfig command
Gspace# ifconfig wlan0 10:20:30:40:50:60The attacker needs to know a trusted Mac address. However if she is patient ,she can simply sniff the network and log all Mac addresses that are in use. When one of them stops transmitting for a while,she can steal it and the AP will not be wiser..


Leave a Comment